What's So Special About PKCS#1 v1.5? And The Attack That Just Won't Go Away! | by Prof Bill Buchanan OBE | ASecuritySite: When Bob Met Alice | Medium
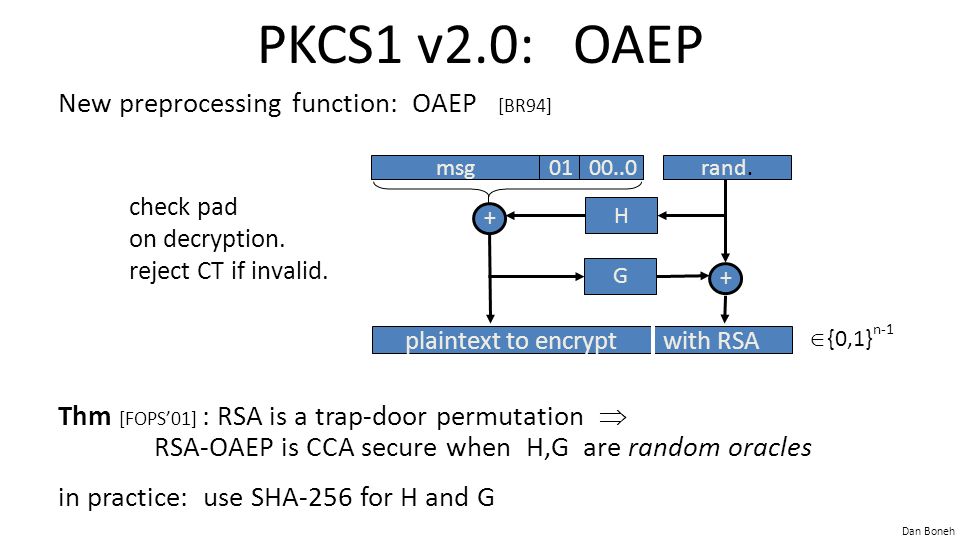
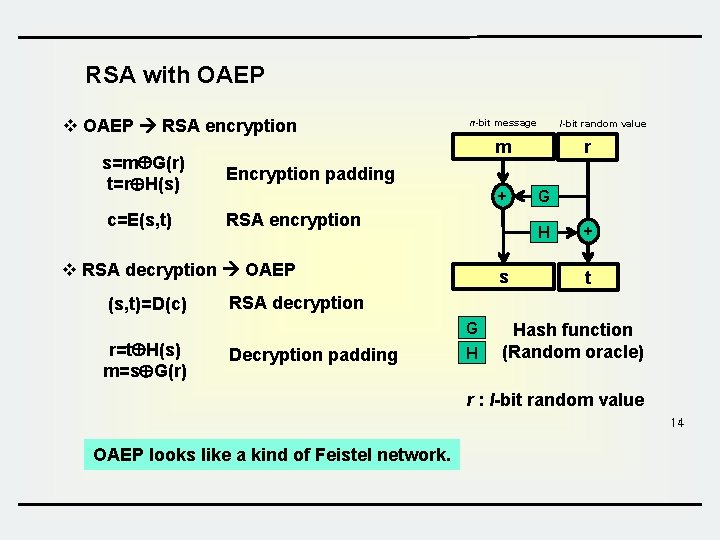
Dan Boneh Public Key Encryption from trapdoor permutations PKCS 1 Online Cryptography Course Dan Boneh. - ppt download
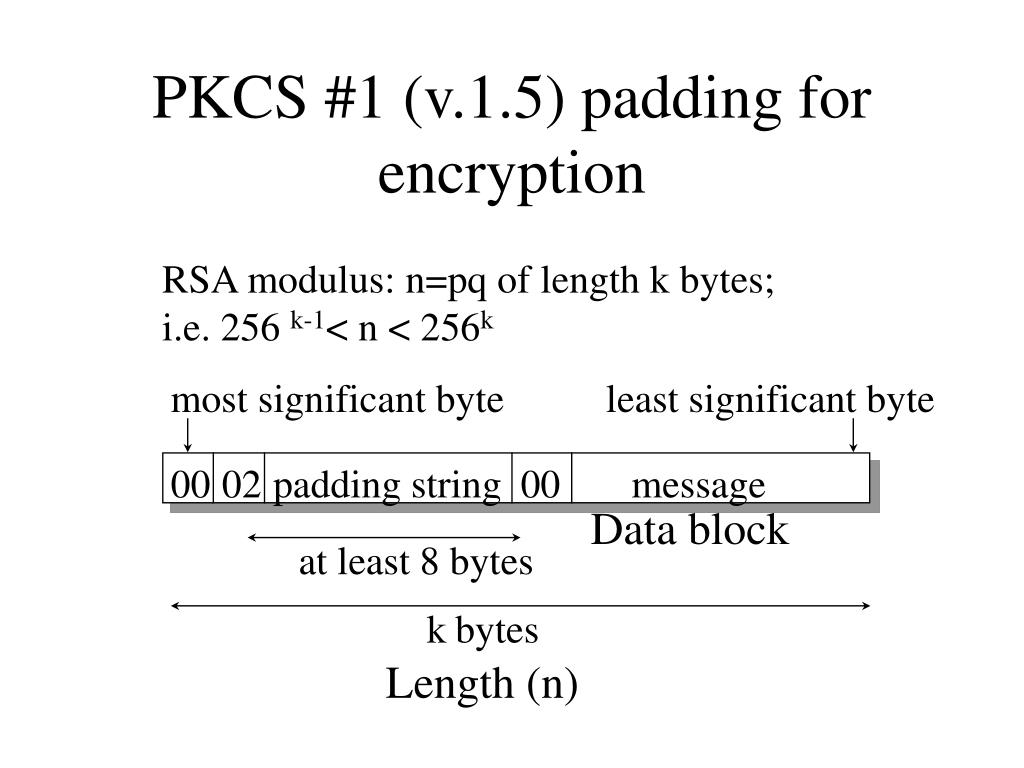
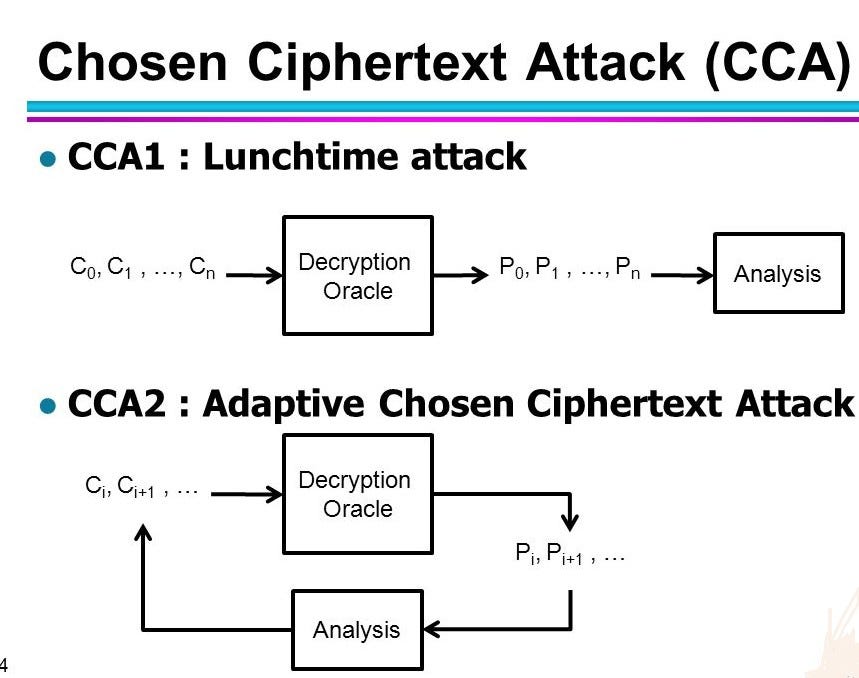
PPT - Chosen-Ciphertext Attacks Against Protocols Based on the RSA Encryption Standard PKCS #1 ( Public-Key Cryptography Stand PowerPoint Presentation - ID:1301747
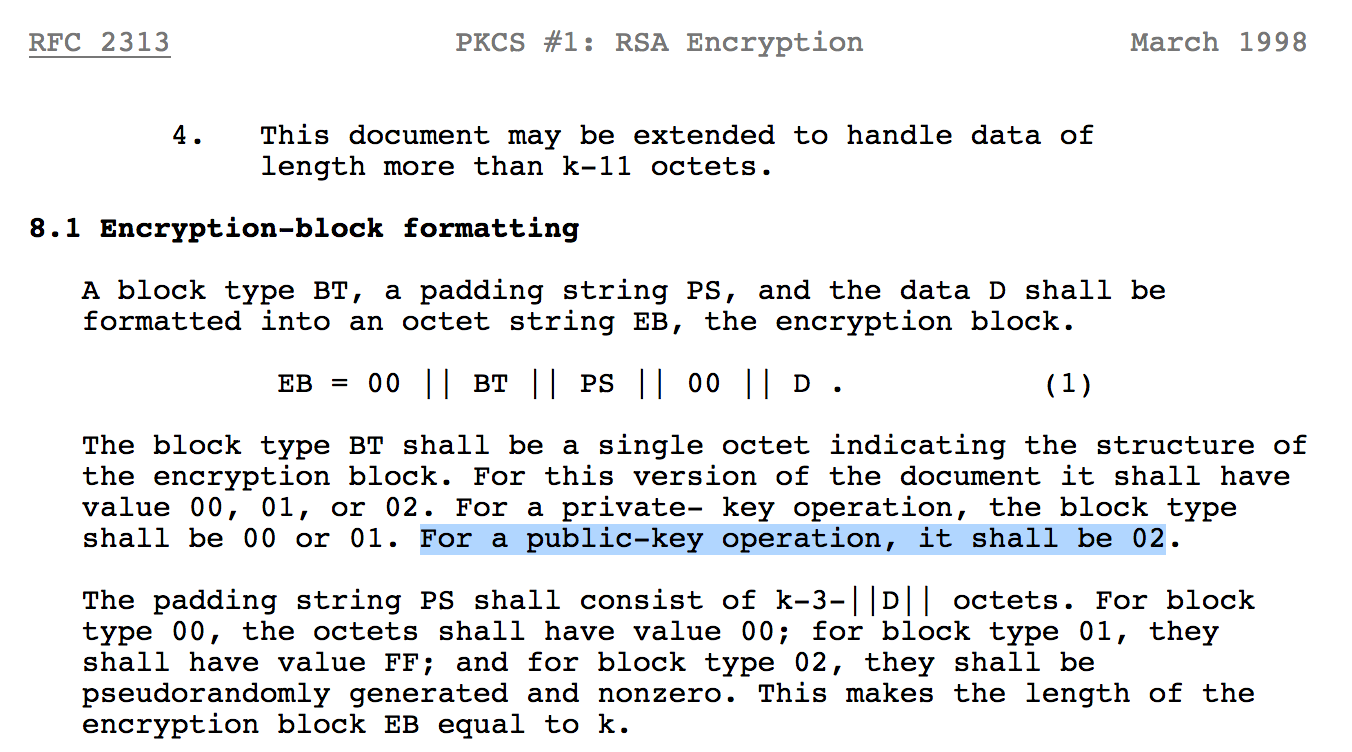
Robots and Random Oracles: The Good and The Bad of Public Key Cryptography | by Prof Bill Buchanan OBE | ASecuritySite: When Bob Met Alice | Medium

3: PKCS#1 v1.5 padding applied to a 16-byte long symmetric key padded... | Download Scientific Diagram

cryptography - How can one encrypt content using RSA for Chilkat in C# and decrypt it in Java? - Stack Overflow